What is EMS Escalation
Our Exploitation Maturity Scoring (EMS) system tracks several key indicators of increased risk. When a vulnerability is associated with any of the following, it triggers an EMS Escalation:- Ransomware: This escalation indicates that the vulnerability is known to be actively exploited by ransomware groups.
- CISA KEV (Known Exploited Vulnerabilities Catalog): This escalation signifies that the vulnerability has been added to the Cybersecurity and Infrastructure Security Agency’s (CISA) KEV catalog. The KEV catalog lists vulnerabilities that CISA has evidence of being actively exploited in the wild.
- POCs (Proof of Concepts): This escalation is triggered when a proof-of-concept exploit for the vulnerability becomes publicly available. A POC demonstrates that the vulnerability can be exploited, even if it’s not yet used in widespread attacks.
- Public Exploits: This escalation indicates that functional exploit code for the vulnerability has been released publicly. This is a step beyond a POC, often meaning the exploit is more refined or easier to use.
- Weaponized Exploits: This is the highest level of EMS Escalation, indicating that the vulnerability is not only being actively exploited but is also part of known attack tools or malware campaigns. This means the exploit has been integrated into a “weapon” used by attackers.
Where to view EMS Escalations
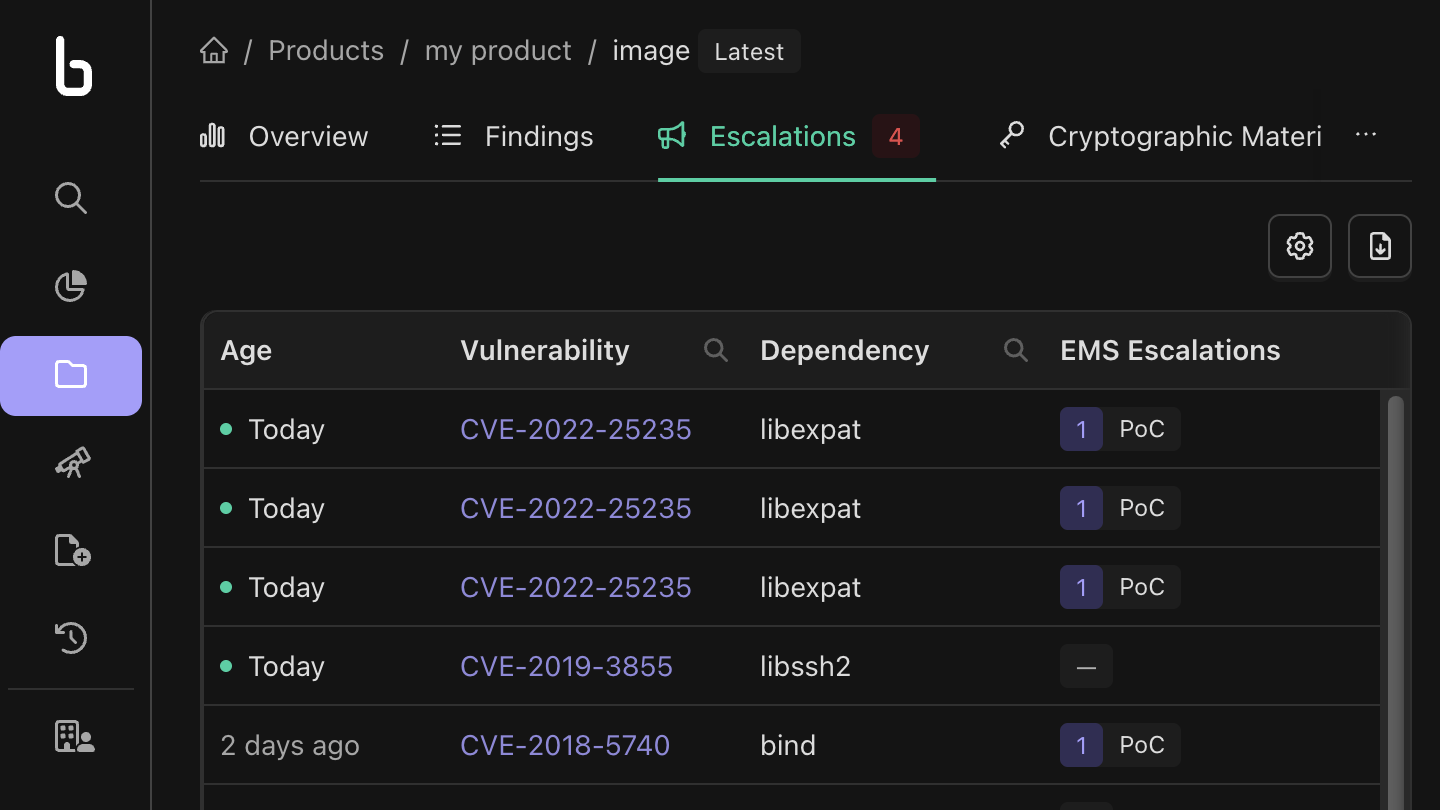
- Chronological Event Tracking: To see a detailed, time-ordered list of EMS Escalation events for a specific image, navigate to the Image Overview page. Within this page, you will find an Escalations tab that provides a chronological history of all exploitation maturity changes.
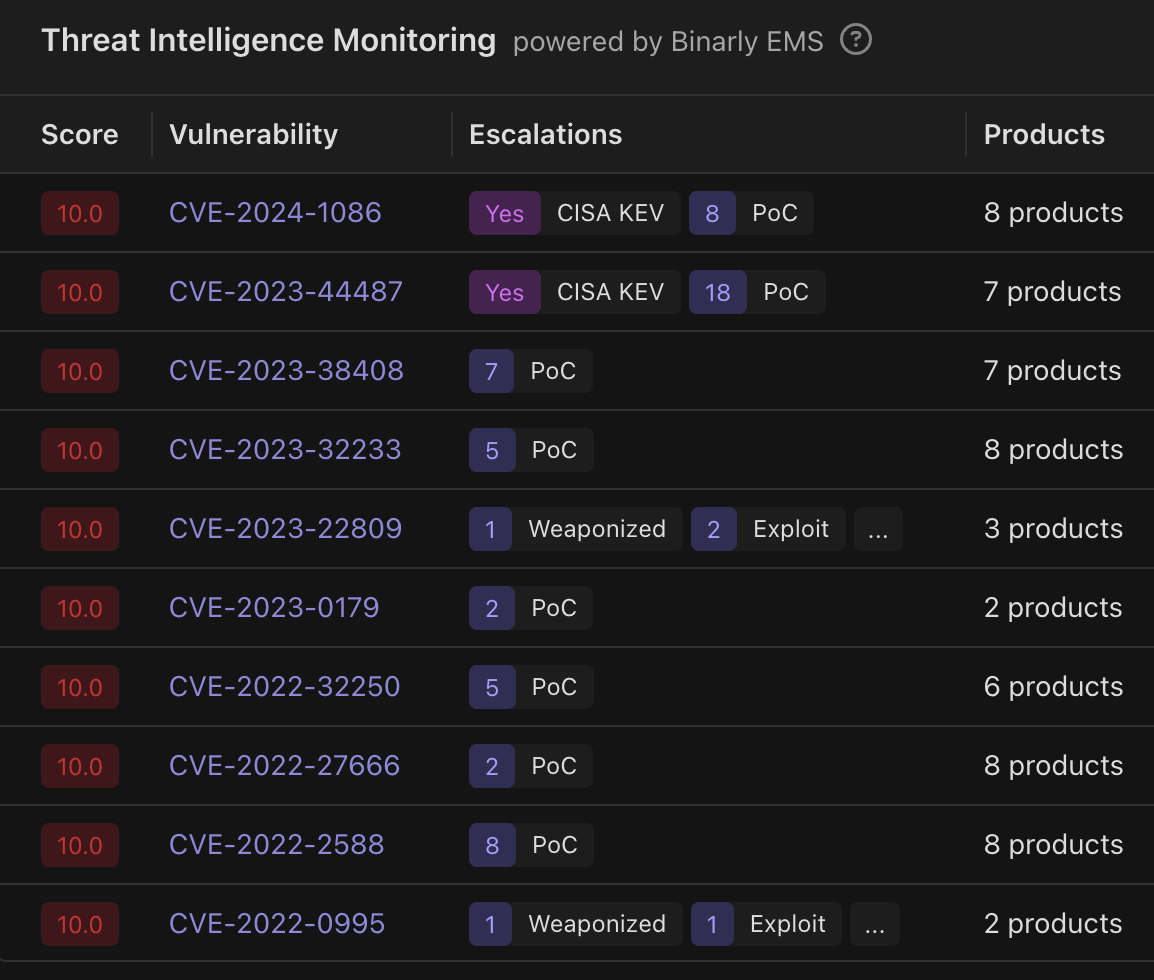
- Threat Intelligence Monitoring Widget: This widget can be found on the global dashboard and Image Overview and shows top 10 (by EMS Score) most pressing vulnerabilities present within the platform.