The Challenge of Managing Software Supply Chains
In today’s business environment, most enterprise companies rely heavily on third-party software, whether sourced from commercial vendors or open-source communities. This software is often integrated into their own products, which are then delivered to customers. While this approach accelerates development and reduces costs, it also introduces significant challenges:- Accountability to Customers: Companies are responsible for the security and quality of the products they deliver. Any vulnerabilities or risks in third-party software can translate into brand damage, compliance violations, and customer dissatisfaction.
- Managing Risk Internally: Consuming unvetted third-party software—whether proprietary or open source—exposes the company to potential security risks, hidden vulnerabilities, and operational disruptions.
Key Problem: Lack of Visibility and Control
Most third-party software today arrives in pre-packaged binaries, often without access to source code. Even when source code is available, reviewing it thoroughly is labor-intensive, costly, and impractical for fast-moving organizations.
- How can a company ensure the software it imports is secure, compliant, and free of vulnerabilities?
- How can it guarantee the products it exports to customers don’t introduce risks or reputational damage?
Binarly: Automating Software Vetting for Enterprises
Binarly addresses this critical gap by providing automated tools for software vetting and risk management. Think of Binarly as a border control system for your company’s software supply chain—ensuring safety, compliance, and trust at every stage.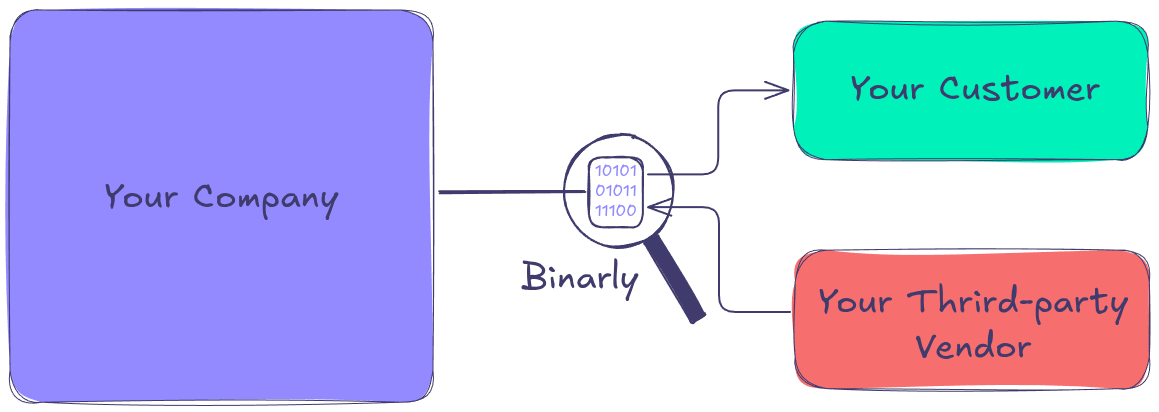
How Binarly Solves the Problem:
-
Automated Risk Assessment:
- Binarly scans software packages (including binaries) to detect vulnerabilities, malicious code, and compliance issues.
- No reliance on source code is required, making it faster and more effective than manual reviews.
-
Streamlined Import/Export Control:
- For software imports: Ensure all third-party software is secure before integration into your company’s systems or products.
- For software exports: Confirm that your products meet the highest standards of security and compliance before delivery to customers.
-
Cost and Time Efficiency:
- Binarly reduces the time and resources needed for software vetting, empowering your engineering and security teams to focus on strategic priorities.
- By automating the process, Binarly eliminates human errors and reduces costs associated with manual analysis.
-
Scalable Security:
- Whether you’re managing a handful of vendors or a complex, global supply chain, Binarly’s tools provide consistent, scalable protection.
Why This Matters for Your Business
For product managers, managing software risks is not just a technical challenge—it’s a business imperative. Unvetted third-party software can lead to:- Security Incidents: Vulnerabilities in imported software can create entry points for attackers.
- Regulatory Non-Compliance: Violating standards like GDPR, HIPAA, or ISO 27001 can result in fines and reputational damage.
- Brand Damage: Delivering products with hidden risks erodes customer trust and impacts market competitiveness.
- Meets compliance requirements.
- Reduces security risks.
- Maintains trust with customers and stakeholders.