Product Security & Compliance
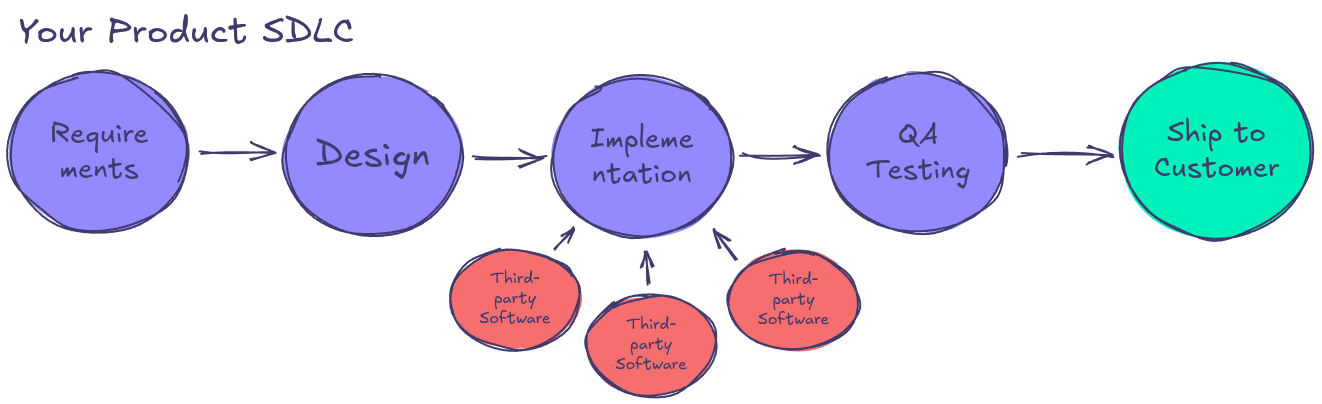
- Problem: Traditional source code scanning tools fail to analyze pre-compiled binaries, firmware, and transitive dependencies creating major security blind spots.
- Solution: The Binarly Transparency Platform scans compiled binaries (instead of just source code), detecting vulnerabilities in third-party libraries, embedded software, and firmware that developers may not have source access to.
- Impact: Organizations can eliminate security risks before release, preventing vulnerabilities and supply chain threats from reaching production. This proactive approach helps mitigate potential brand damage and costs afterwards.
Procurement & Third-Party Software Validation
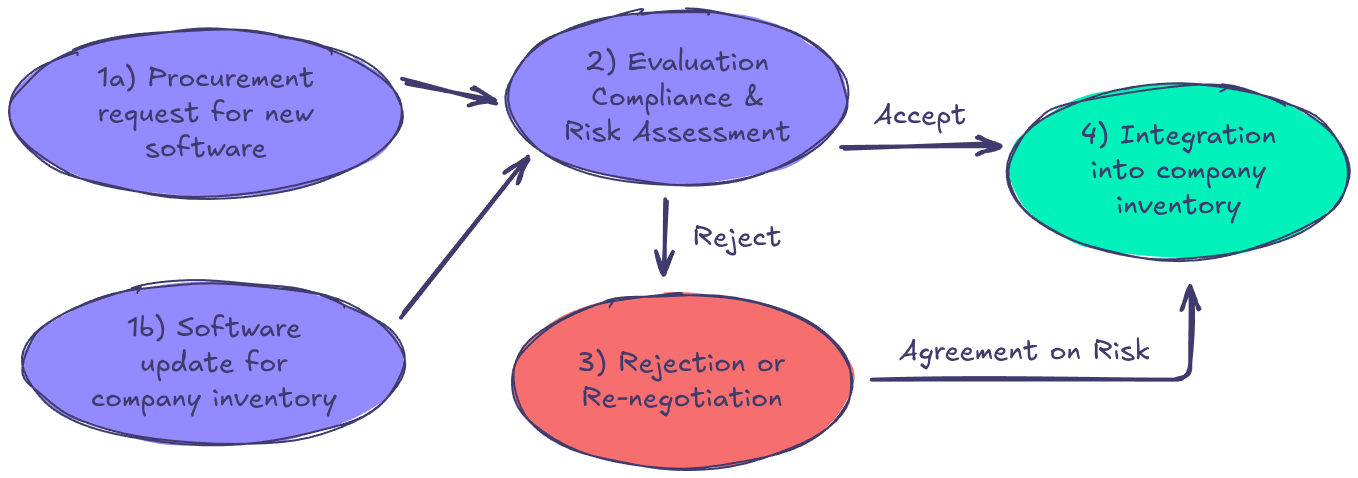
- Problem: Many organizations integrate third-party software, firmware, and hardware components into their infrastructure without fully validating their security. This can introduce hidden vulnerabilities, backdoors, and supply chain compromises.
- Solution: The Binarly Transparency Platform scans vendor-supplied binaries before procurement, ensuring they are free from known and unknown security threats. This prevents organizations from purchasing or integrating compromised components or products.
- Impact: Security teams gain visibility into third-party software risks, reducing the likelihood of supply chain attacks, compromised firmware, and regulatory non-compliance.
Cryptographic Export Control
- Problem: Weak or misconfigured cryptographic implementations expose systems to data breaches, supply chain attacks, and regulatory non-compliance. Organizations often lack visibility into third-party and embedded cryptographic assets, increasing security risks.
- Solution: The Binarly Transparency Platform analyzes binary files to detect hardcoded keys, insecure encryption algorithms, and weak cryptographic protocols. It generates a CBOM to provide full cryptographic inventory transparency and assesses compliance with NIST PQC standards (FIPS 203, 204, 205) to help organizations proactively transition to quantum-safe encryption.
- Impact: Organizations can eliminate cryptographic vulnerabilities, reduce the risk of data exposure, prevent supply chain threats, and ensure compliance with NIST, FIPS, GDPR, and emerging PQC regulations.