Image Report Examples
Image Summary PDF Report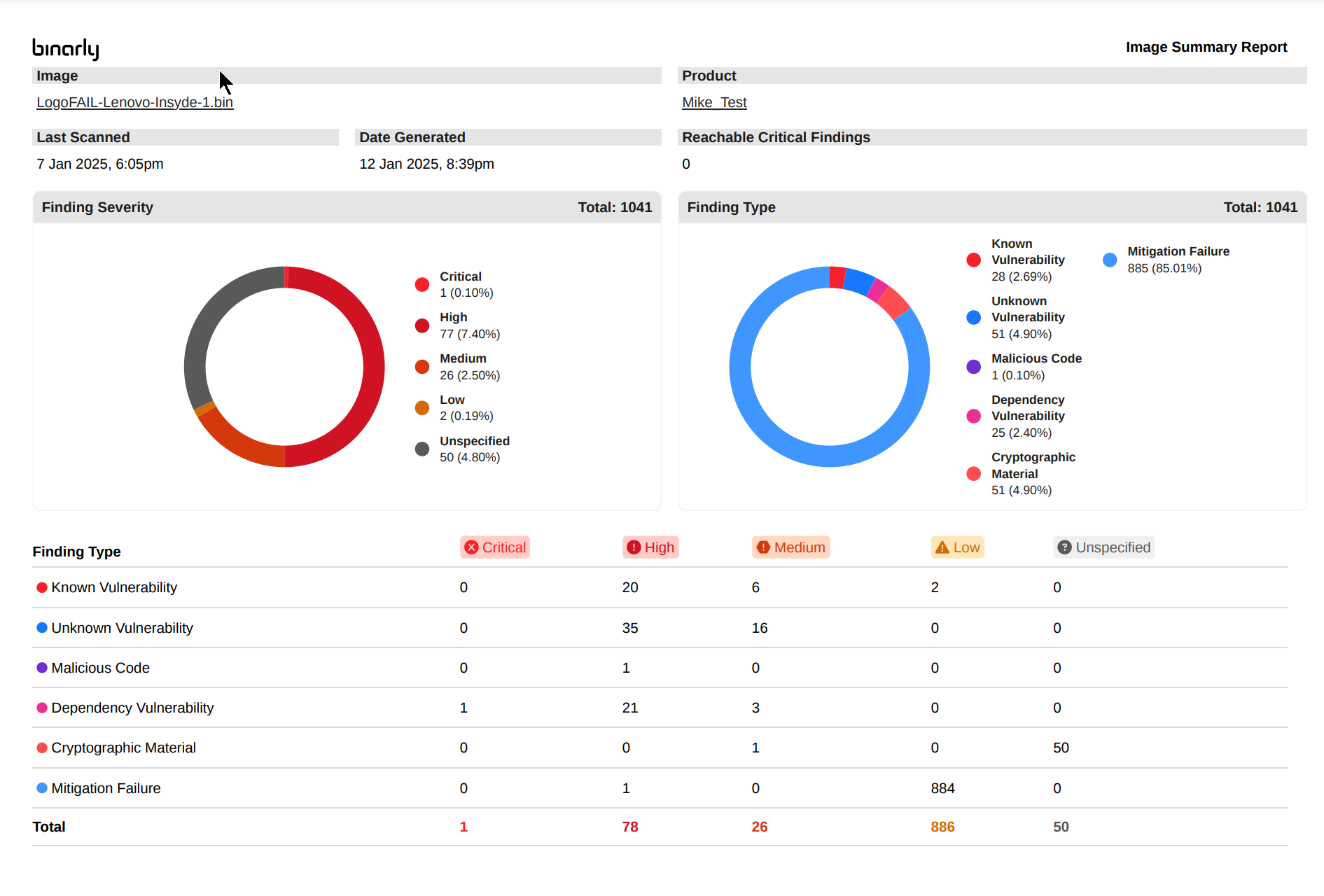
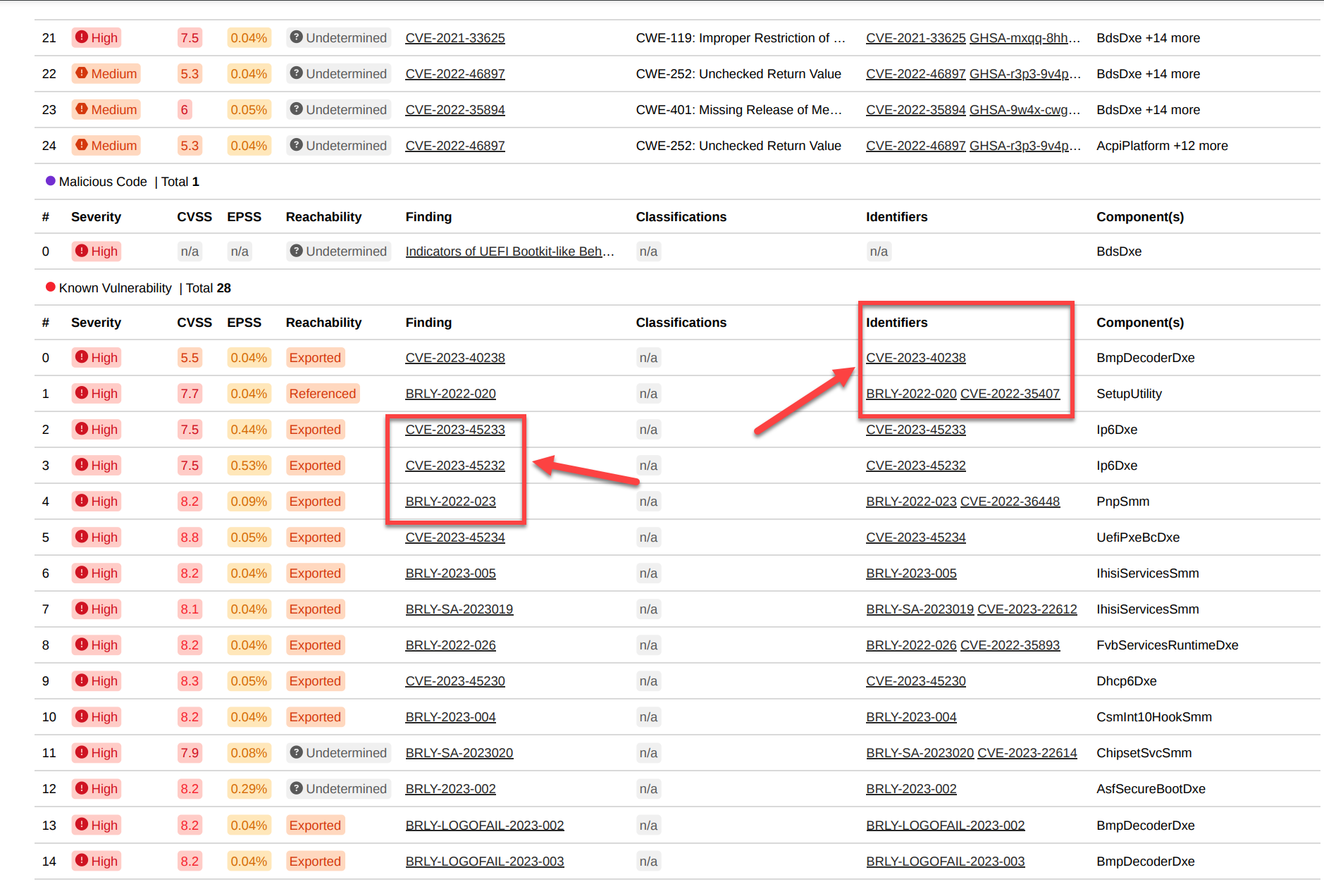
Finding Detail Reports
Reports generated from within the detail view of a finding are typically used to convey a highly detailed View of the vulnerability including all aspects of the finding. this provides the recipient with all the information necessary toFurther investigate or take actions to remediate or mitigate the finding. This output will include all industry references (CVE , CVSS, CWE, EPSS), descriptions, and component details for the selected finding. For specific finding types Known, Unknown vulnerabilities and Malicious Code) extended component vulnerability location details will also be included in the report. This includes Pseudo code representations of the findings where applicable.PDF finding Output Examples
- Unknown vulnerability finding detail report
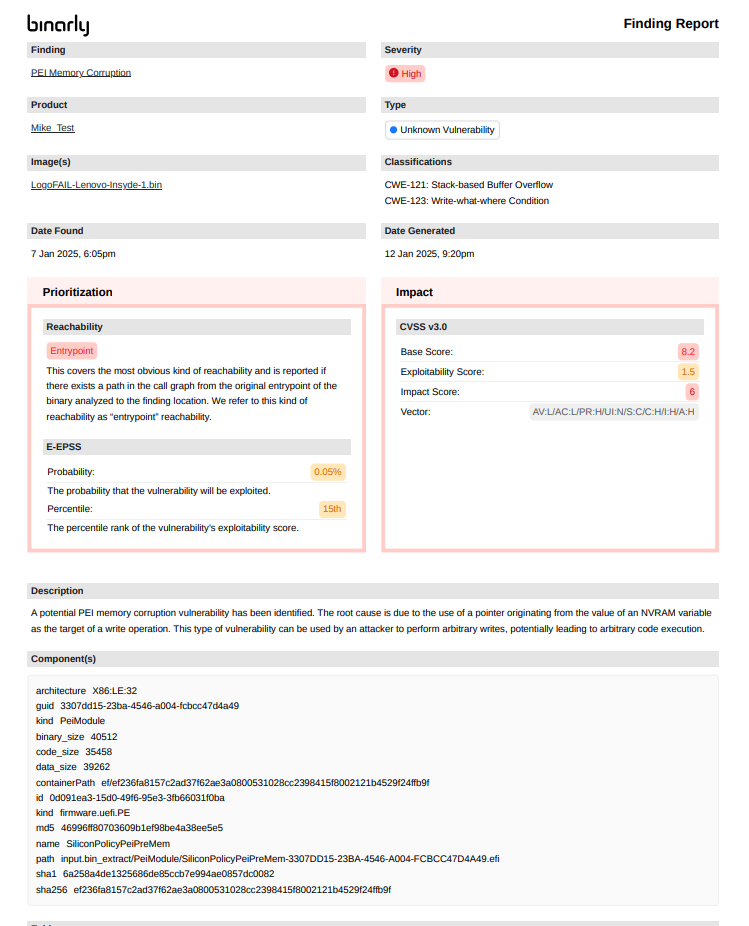
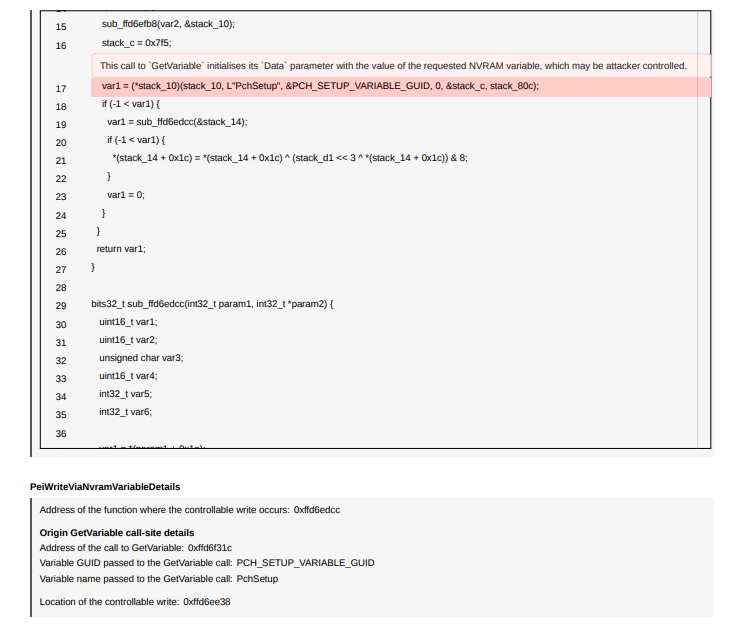
- Dependency Finding Detail Report
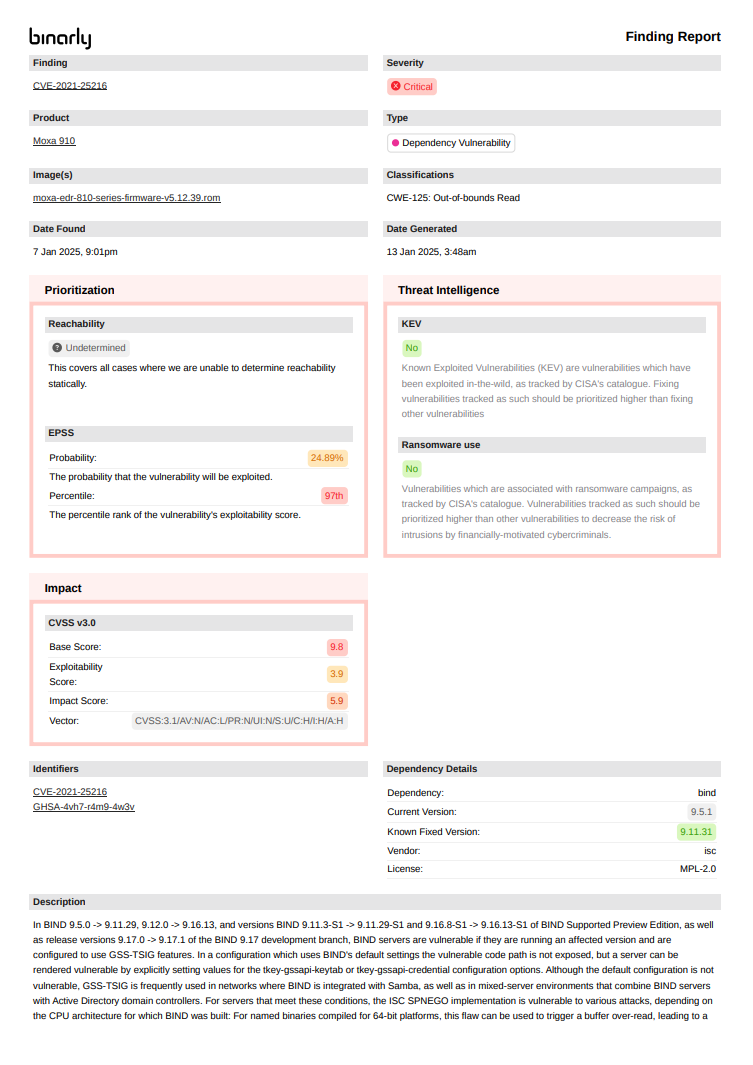
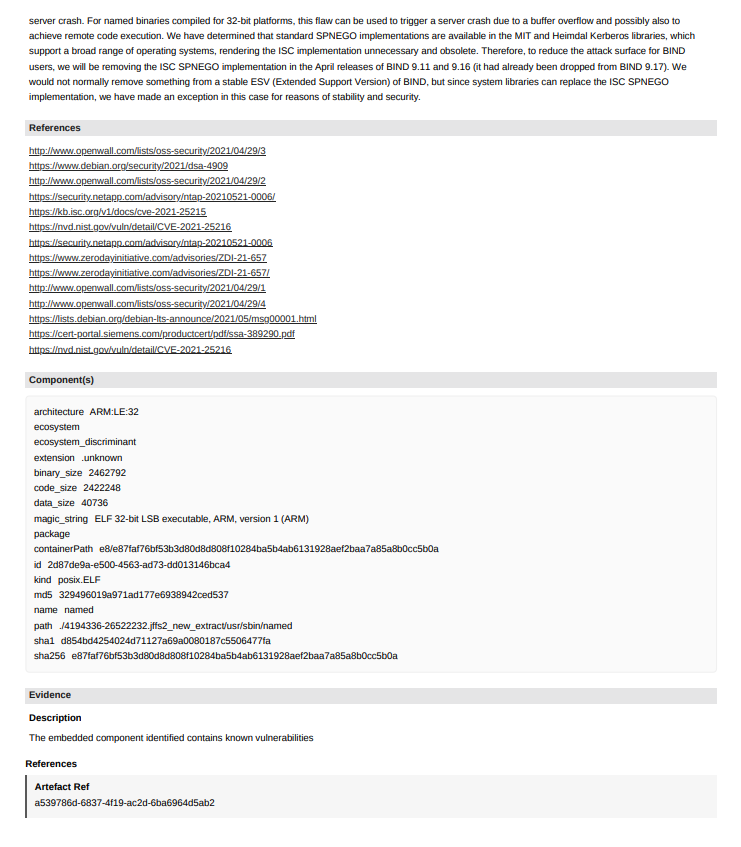
- Cryptographic Material finding Detail Report
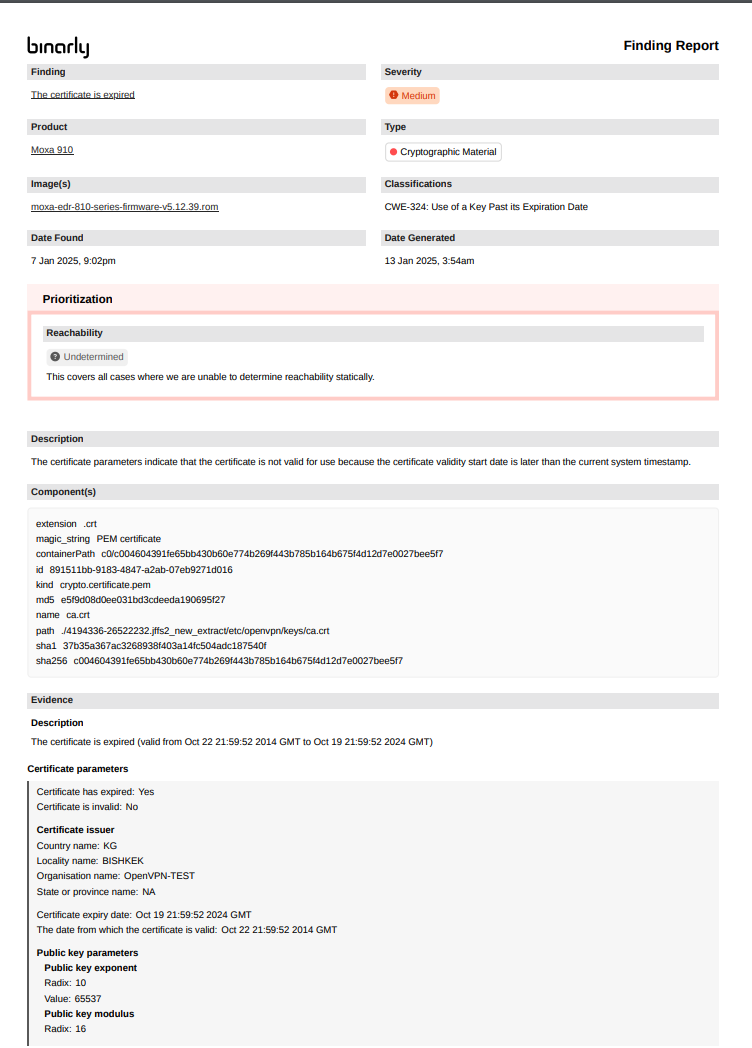
JSON finding Output examples
- Known vulnerability finding detail output
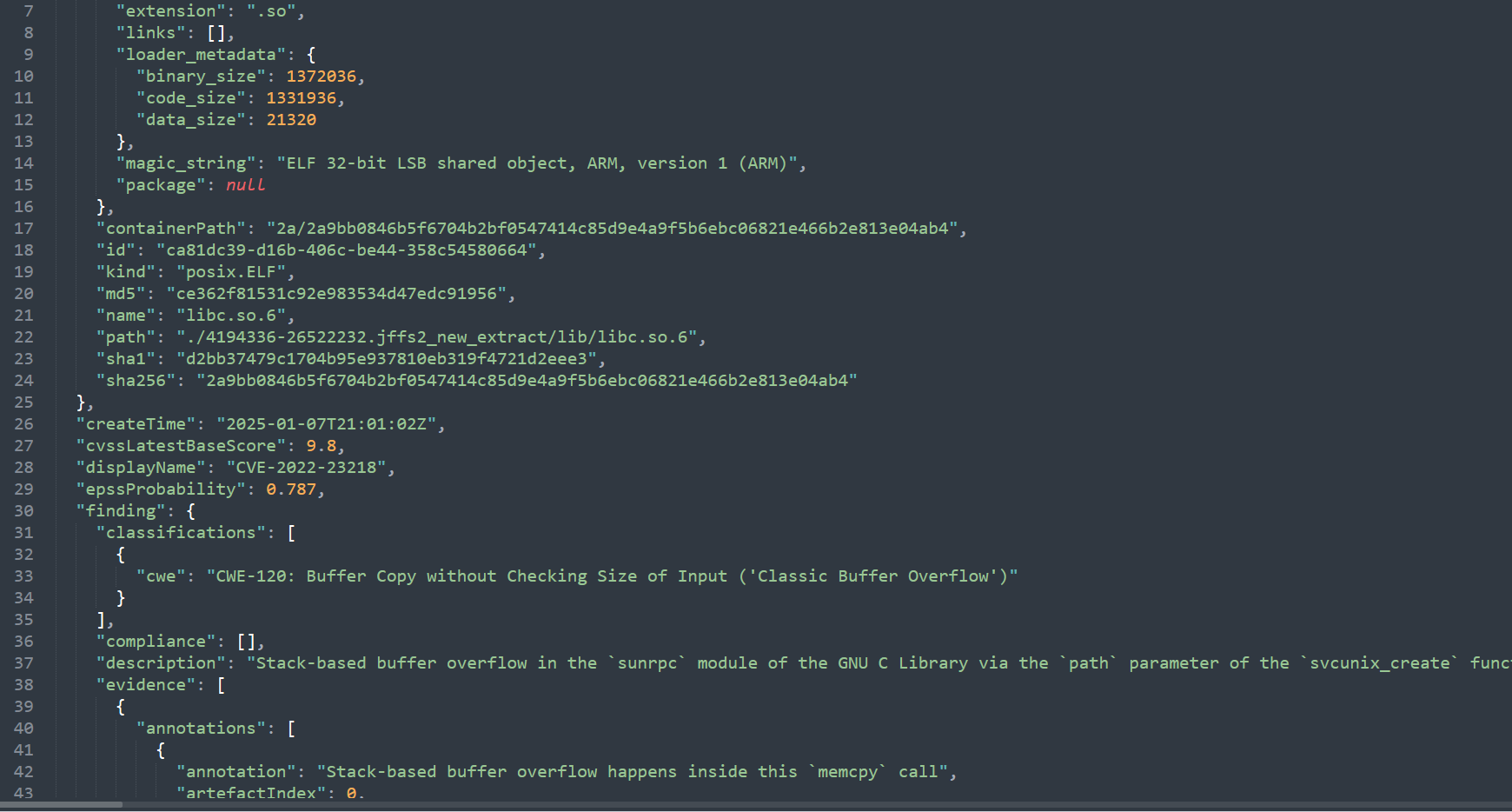
- Dependency finding detail output
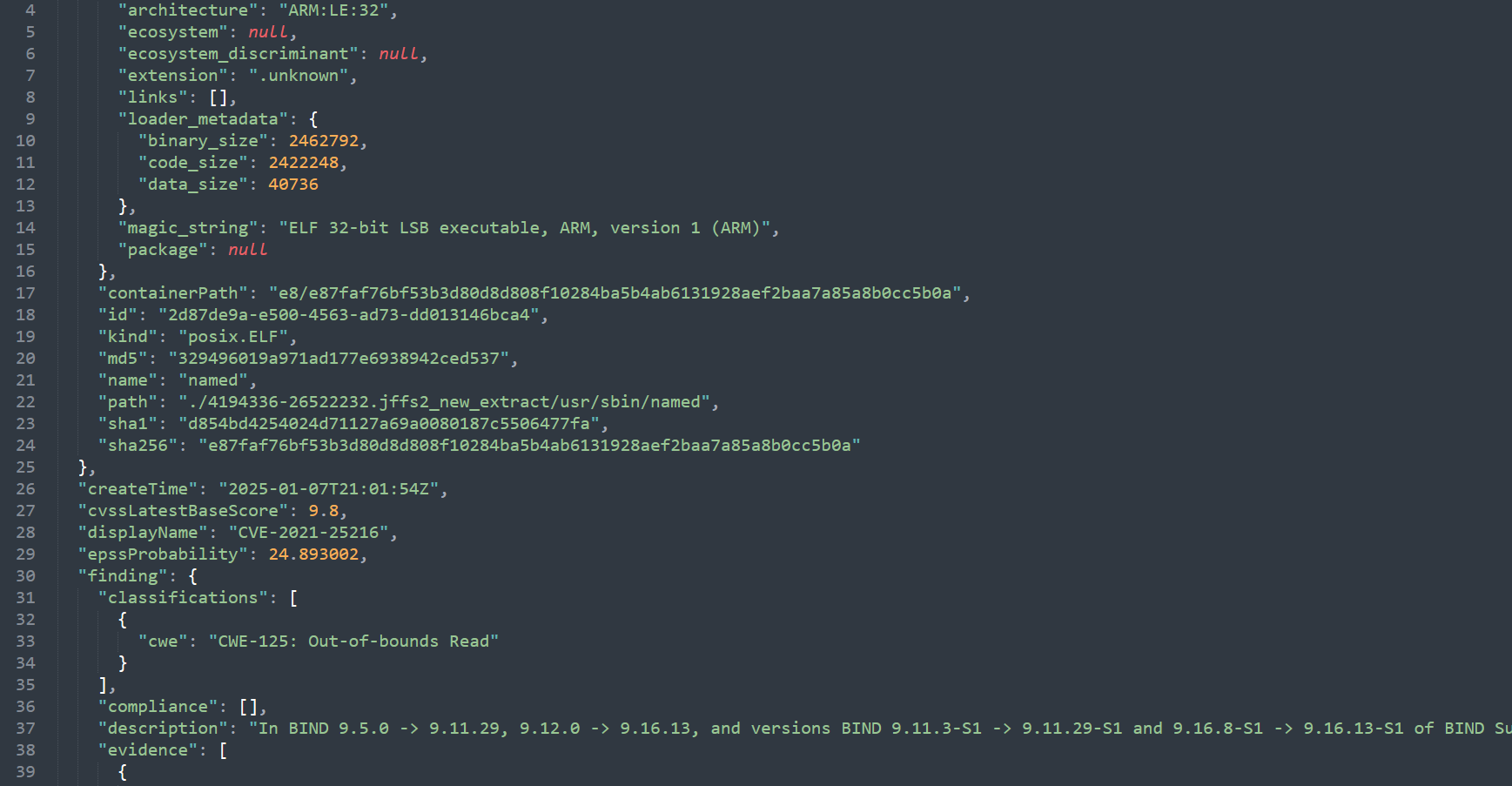
- Cryptographic Material finding detail output
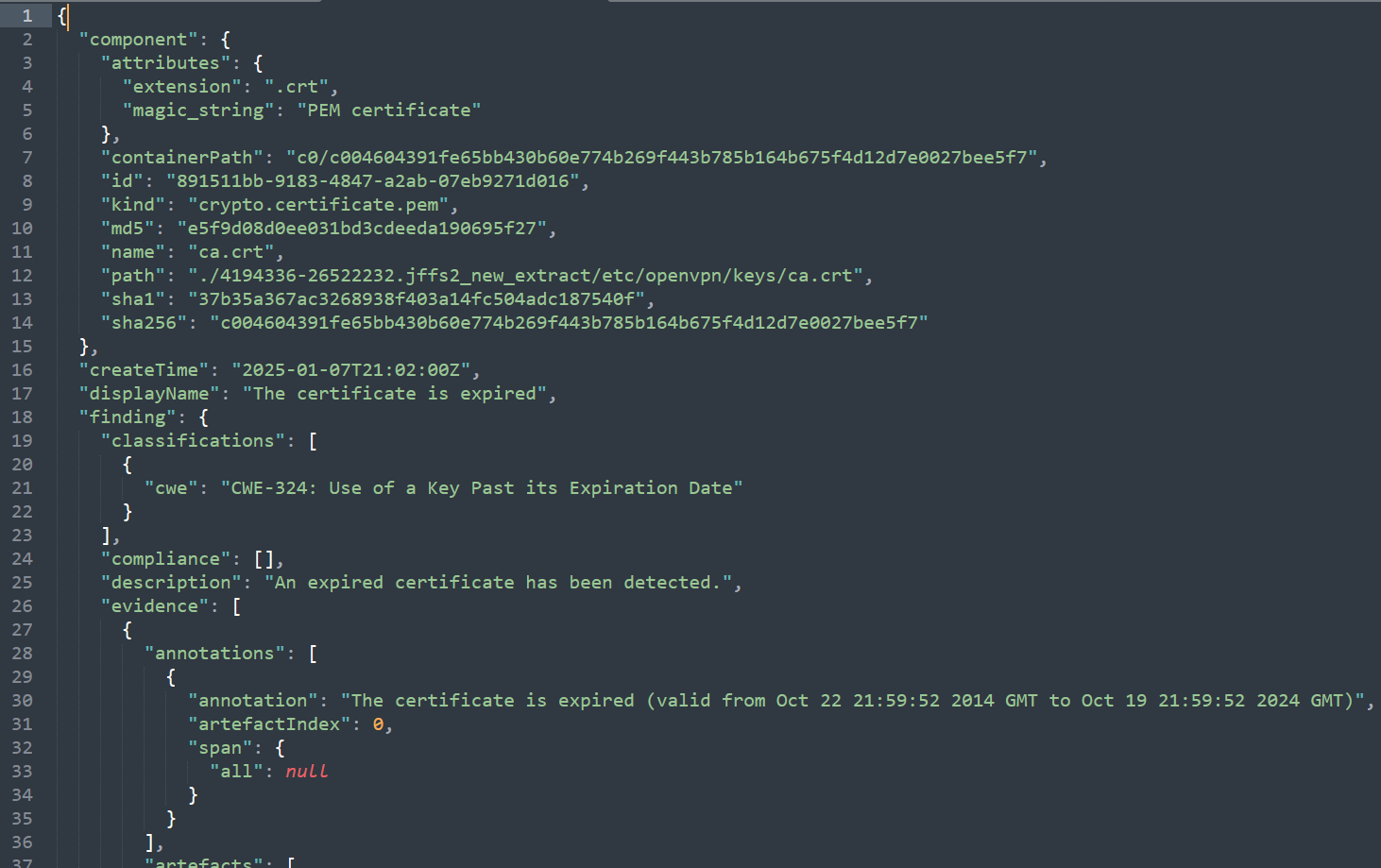
Bulk Finding Export
Findings can be exported as CSV files. This bulk export includes all columns from the findings grid, as a direct export of what the findings grid currently displays.