Advisory Content
Each automatically generated advisory includes technical details about the UEFI vulnerability: a summary with a concise description of the security issue, affected component details including the vulnerable UEFI module’s name, GUID, and hash values, and a risk assessment in the form of the vulnerability’s CVSS vector and score. Below is an excerpt of a generated advisory.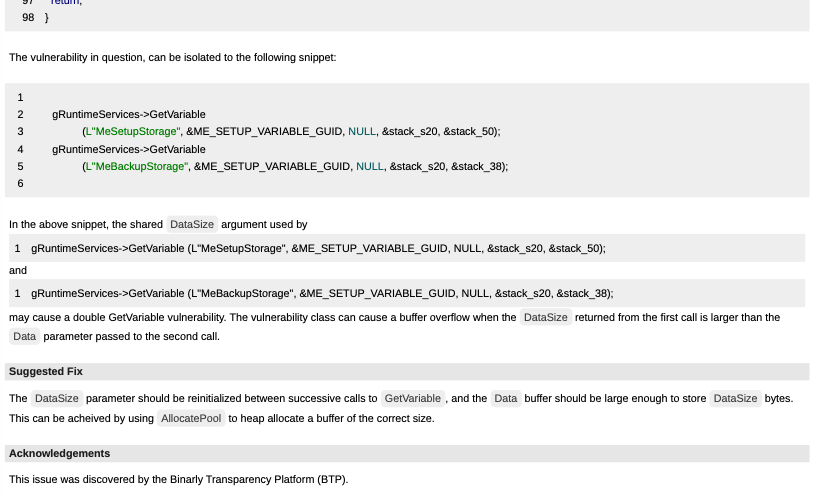
Generating Advisories
The Automatic Advisory can be generated from the finding details page (see below).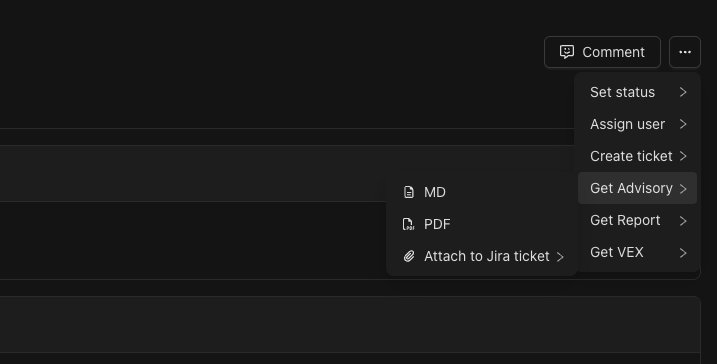
- Navigate to the finding details page for a UEFI vulnerability
- Click the three-dot menu (…) in the finding details interface
- Select Get Advisory from the dropdown menu
- Choose your preferred output format:
- PDF: Formatted document suitable for formal distribution and presentation
- Markdown: Text-based format ideal for integration with documentation systems or further editing