Use Case: Product Security & Compliance
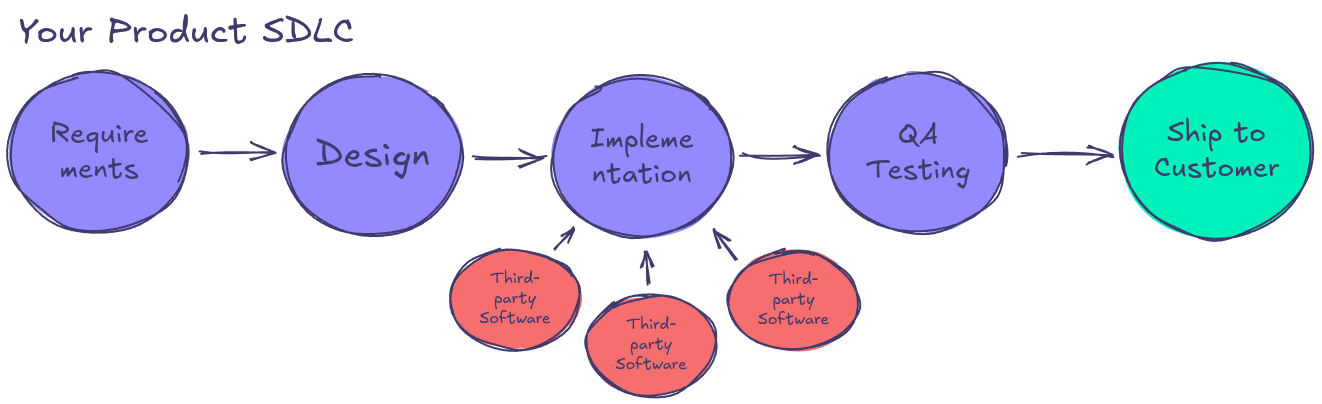
Without Security Checks – A Blind Spot for Third-Party Dependencies
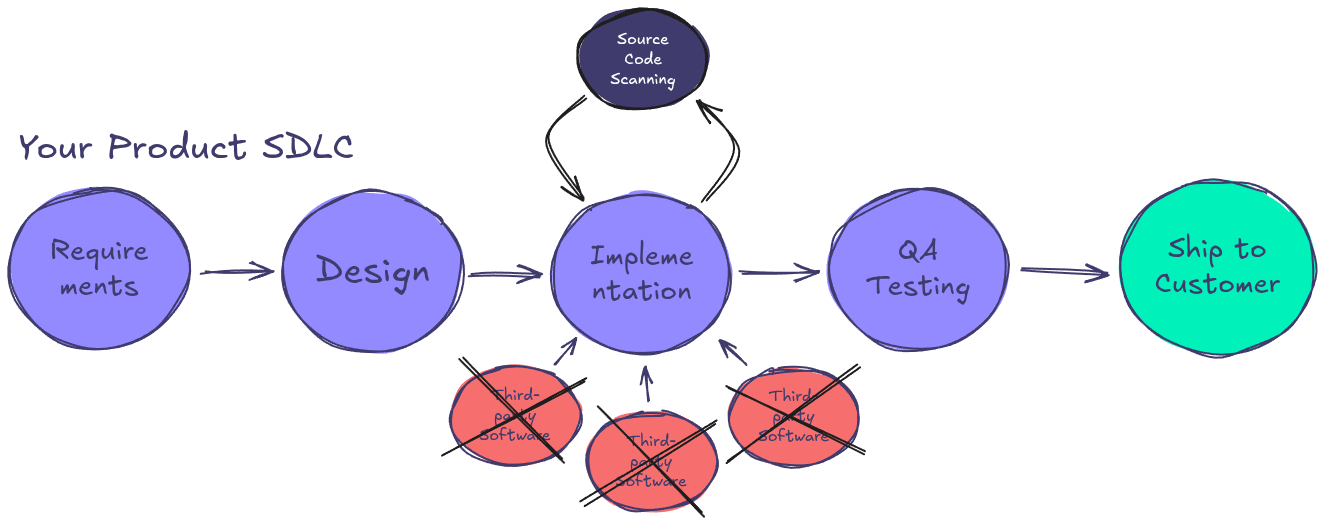
Source Code Scanning – The Visibility Gap
SDLC with Binary Scanning – Closing the Gaps
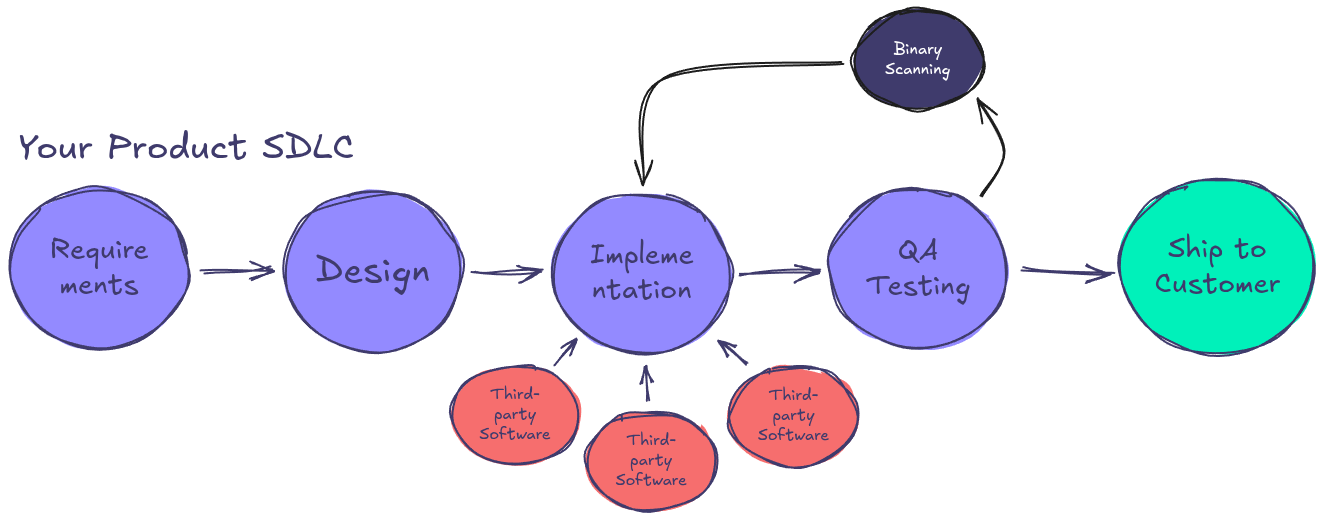
- It detects vulnerabilities in third-party and transitive dependencies that source code scanning cannot analyze.
- It provides visibility into proprietary and precompiled software components, including drivers, firmware, and closed-source libraries.
- It is easier to implement because it does not require access to the original source code, eliminating the need for vendors to disclose proprietary code.
- It integrates later in the SDLC, allowing security teams to validate software integrity right before release, reducing last-minute surprises.